If you’re overwhelmed by the vast number and types of optical features available to add security to identity documents, you’re not alone. In this paper, a group of experts from the Secure Identity Alliance (SIA) clarifies the options—and when and how to apply them.

While technology is an important enabler, successfully implementing the end-to-end seamless border vision is a complex proposition that involves multiple stakeholders and requires supporting common standards alongside harmonised regulatory frameworks.
Having explored the vision and the technology innovations and advances being utilised today to support the implementation of seamless border programmes around the globe, we’ll now look at what’s involved in making this happen ‘for real’.
One thing is for sure. Initiatives currently underway highlight how implementation is a complex and multi-faceted proposition that goes way beyond simply planning to deploy new standalone systems and technologies and ‘hoping for the best’.
For a start, building a successful IT system that supports seamless travel involves deep collaboration between multiple stakeholders including border authorities, air and sea ports, land-based border points and carriers – including train and bus operators – and deep integrations with a multitude of other systems.
All of which will entail the redesign of business processes, the training of personnel in these new protocols, and careful planning to manage the operational impact of these changes. Plus, systems will need to be backwards compatible and future-proofed to support potential further technology innovations on the horizon. The discipline of change management and engaging comprehensively with stakeholders should include travellers, who need to be able to use the new solutions. Good two-way communication will all be important for achieving a successful outcome within planned timeframes.
But that’s not all. As technology increasingly forms an essential part of border control and international travel processes, the need for excellent cyber resilience and highly reliable IT systems and infrastructure will grow. Contingency plans need to be in place to handle unexpected downtime events, which could cause major disruption.

Imagine being denied entry to a foreign country because the electronic chip in your travel document is considered vulnerable and you would have to request a visa before traveling there? Because travel documents usually have a 10-year validity, this is a valid concern and is the reason why we consider micro-controllers (often called chips) in secure documents to be high value components.
As one of the most basic instances of the advanced IT solutions available in the industry, secure software embedded in ePassports and keeping them safe from their Cyberattacks are the object of deep concern and attention, especially with the increased adoption of digital ID, often derived from a secure electronic document such as a passport.
Cybersecurity is an ever-evolving concern. Setting up a secure identity document project relying on highly certified products is a necessary practice but not sufficient for protecting identities from future Cyberattacks. Active monitoring and anticipation of Cyber threats is critical to protect sensitive assets. Such threats include eavesdropping, cloning, or extracting highly confidential fingerprints from the electronic chip.
Decades of security progress have been framing an always-improving environment focused on a single objective: defining and maintaining a Cybersecurity framework to deploy secure embedded solutions in electronic ID documents.
The next step is to look beyond Cybersecurity and focus on Cyber resilience, which refers to an entity's ability to continuously deliver protection, despite adverse events. This combines information security, business continuity, and organizational resilience. This is particularly relevant for governmental programs, who should continue to issue secure identity documents to their citizens at any point in time.
Concretely, the future Cybersecurity of ID documents like ePassports depends on the ability to update, in the field, the secure embedded software (for example algorithms used for the various security mechanisms) protecting the data stored in the chip – with no need to issue a new document.
How does Cybersecurity work in an ePassport scheme?

Post pandemic, international traveller numbers are ramping up and are expected to continue to surge. Meanwhile, staff shortages, stricter travel processes and additional document checks and pre-travel enrolment requirements have all had an impact on how quickly travellers are processed at air and sea ports as well as land borders and crossing points. Combined, these can result in long queues at points of departure/arrival as travellers wait to be processed and undergo entry and exit checks.
For border control agencies, admitting genuine travellers as quickly and efficiently as possible while identifying travellers who may not be welcome is a top priority. Meanwhile, port authorities need to optimise passenger flows in order to boost throughput and minimise congestion and passenger wait times. Creating the additional capacity needed to support the anticipated future growth in passenger numbers.
The good news is that in recent years, advances in digital connectivity have spurred governments and private sector organisations on to introduce technology-based and secure-by-design solutions that both boost the efficiency and security of border control processes while elevating the traveller experience.
Let’s take a look at some of the technology advances already making an impact when it comes to enabling a frictionless journey experience for passengers, while reducing the cost and complexity associated with capturing accurate and verifiable data before a visitor arrives at a border – and ideally before they even leave their country of origin.

Long term shifts in traveller numbers are driving governments around the globe to rethink how to manage the smooth and compliant movement of a growing number of travellers through ports and across international borders. According to the World Tourism Organisation, more than 900 million tourists travelled internationally last year – a figure that is predicted to hit 1.8 billion by 2030 and 8.2 billion by 2037.
Facilitating the seamless movement of vast numbers of people in the most efficient way possible is just the start of the challenge. Ensuring the security of national borders and citizens is another top imperative—seamless borders aims to deliver an easier passenger journey and improved security, benefiting all stakeholders. This can be a challenge given constraints on space, time and resources. Efficient, seamless borders will be more able to handle high passenger volumes to avoid overloading capacity at ports which can quickly become apparent in long queues inconvenience for everyone.
This is driving industry bodies and governments to press ahead with digitalisation initiatives. Because, as IATA, the trade association for the world’s airlines, notes: “Passenger traffic is projected to double by 2037. We will not be able to handle this growth or satisfy evolving customer expectations with existing airport capacity, current processes, facilities and ways of doing business.”

It is with deep sadness that we have learned about the passing of Ny Andriana Andriantseheno Balsama Heliarson, our colleague and friend Bali. Bali H. Andriantseheno was an early supporter and Advisory Committee Member of the OSIA Initiative since the beginning of the adventure. We want to extend our heartfelt condolences and deepest sympathies to his family.
Debora Comparin, Chair of OSIA Initiative, SIA and Standardisation Expert, Thales
Thanks to co-author Yiannis Theodorou, Head of Digital ID, Tony Blair Institute for Global Change for his contribution to this commentary.
As governments continue to build inclusive digital-ID ecosystems to unlock the value of digital transformation for their people, many are facing the challenge of which related technology solutions to adopt.
In markets that encourage competition and innovation, it is common to see the creation of proprietary, closed and non-interoperable systems when a new industry is formed; remember the days when the phone you bought in Europe could not be used to make or receive calls in the United States? Eventually, though, the forces of supply and demand drive the industry towards harmonised, optimal solutions and common standards.
Today’s identity market is an environment of siloed foundational and functional ID systems, partly built on proprietary technologies. But, as the market matures, new tech solutions are drastically redefining the landscape. Mobile-ID solutions, sophisticated biometrics, cloud computing and other technologies have made it possible to develop integrated national ID ecosystems that are efficient, cost-effective and secure, without necessarily involving centralised databases.
Yet many countries still have a long way to go before they can realise this vision, and their ability to easily switch to new technology partners or providers is severely hampered by the complexity of existing systems or contractual arrangements. For example, if a newly procured digital-ID provider must deal with encrypted biometric templates in an existing database, it would need to access the raw biometric images captured and stored by the previous provider’s systems. If the unencrypted raw images are not available or reliable, the government will likely be forced to re-register the entire population.
Vendor lock-in constrains development because any change is subject to considerable costs and the risk of operational failures. At the same time, to benefit from the latest technologies, governments need to update, adapt and upgrade their legacy systems while having the freedom to choose the most appropriate solutions to meet their needs.
Two main approaches have emerged that offer governments the flexibility and freedom they need: open standards and open-source software.

Landmark qualification enables the ITU-T to normatively reference OSIA specifications
Secure ePassport chips result in trust and efficiency
What is ‘PKI’? An introduction
This article can be downloaded default HERE(2.26 MB)
Trust in passports is essential. PKI technology gives strong evidence that information on a secure passport chip can be trusted. This helps authorities issue more secure passports, increase security and throughput at the border, increase automation and catch identity cheats. It can help airports, airlines and commercial parties to check documents and carry out KYC (Know Your Citizen or Know Your Customer). Genuine passengers are more able to demonstrate their true identity quickly. Conversely, identity cheats stand more chance of being discovered.
Threats of passport fraud are real! A genuine document can be lost, stolen or borrowed and used by someone who is not the holder (an imposter or lookalike). A criminal might try to change the photograph or other data about the holder, to turn a passport into his own travel document (a forgery). A false passport might be manufactured (a counterfeit). Someone may make a false application to obtain a passport (a Falsely Obtained Genuine (FOG)). Or someone may steal blank passports which have not yet been personalised (had the holder’s details applied).
Great care is taken to defend passports from such attacks. This includes strong security on the manufacture, storage and delivery of documents; rigorous testing of new passport applications; and advanced security features in passports so that false documents are difficult to produce or use. See Passport Fraud Trends and Ways to Combat Them (Secure Identity Alliance (SIA), 2021); and ICAO 9303 Part 2: Specifications for the Security of the Design, Manufacture and Issuance of MRTDs (see references).
Secure chips improve security and convenience
Many passports and ID cards contain a chip, holding key data about the document and the holder, including the holder’s facial photograph. All of this data is protected by the issuer who includes a cryptographic digital signature on the chip. This signature, when verified, shows that data on the chip comes from the right source and has not been changed. Only the issuer can produce this signature, but everyone who needs to can verify that the signature and the data match. If so, it can be trusted; if not, it can’t. The complete picture is called a Public Key Infrastructure (PKI).
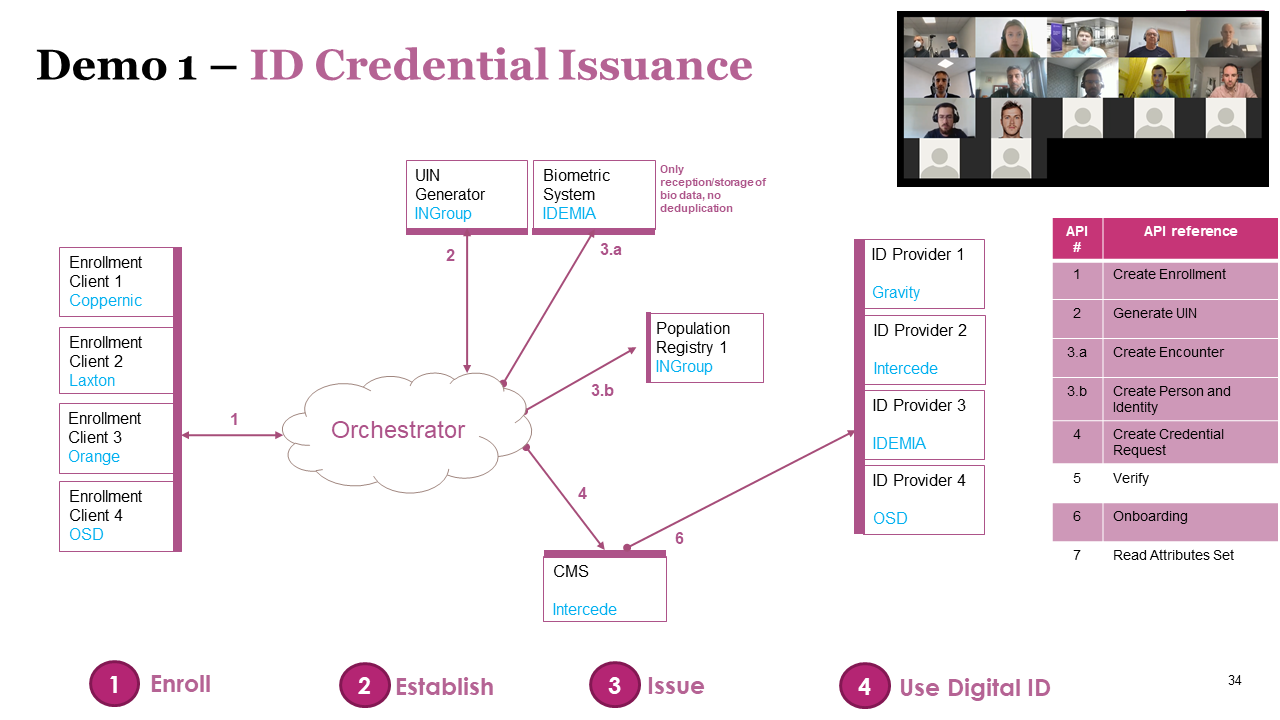
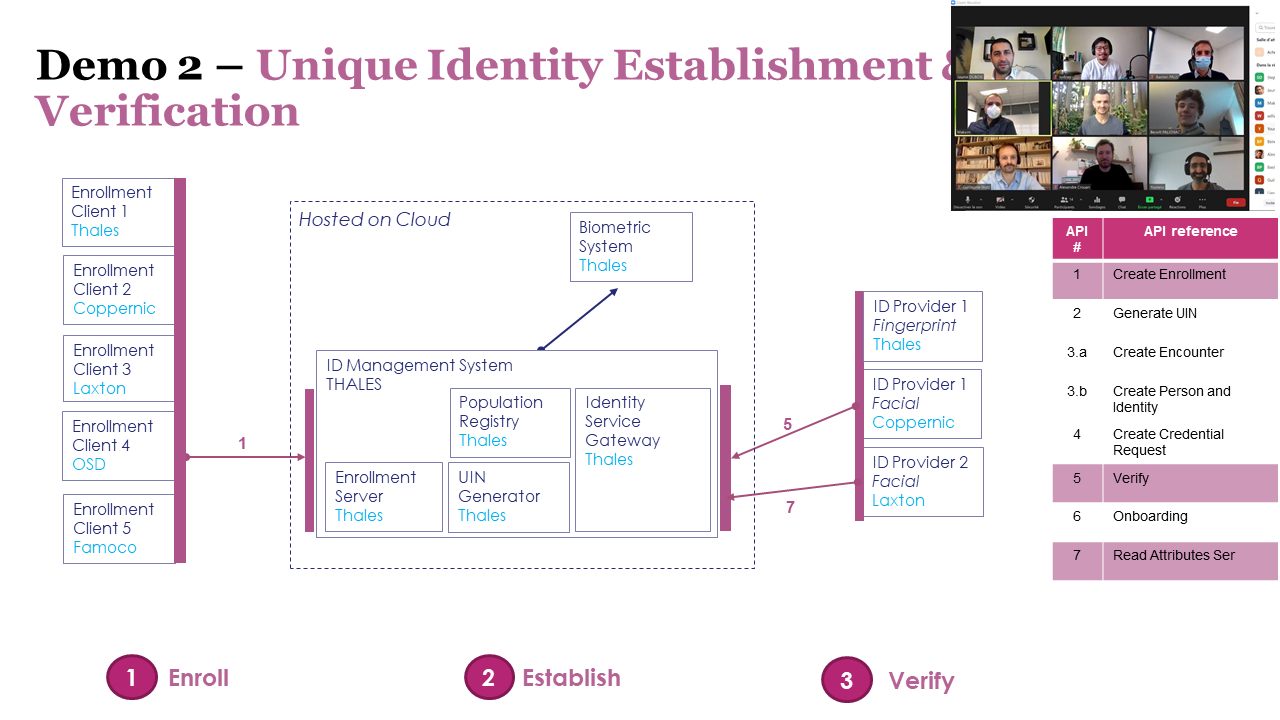
The OSIA qualification program aims at enhancing interoperability of ID management systems, support ID solution development, and address government requirements for OSIA compliance.

Around the globe, trusted legal identity is the foundation of national security, social protection, and economic growth strategies.
As the identity market matures, technologies like digital ID, biometrics and cloud platforms are transforming the ID landscape, making it possible to
- enable national identity models that are truly inclusive and serve the needs of all stakeholders
- initiate the delivery of innovative public and private services.
To capture this opportunity without undue cost or time-consuming integration effort, governments need to be free to evolve, adapt, modernize, and add to their systems with confidence – and without fear of future compatibility issues.
Until recently, however, the initiation of highly functional and interoperable ID systems that are easy to upgrade or change has been constrained by a siloed approach and lack of standardization that made it difficult to connect registries or exchange, consult, or update data between systems.
In 2019, the Secure Identity Alliance (SIA) launched the global Open Standards Identity APIs (OSIA) initiative to address these challenges.
OSIA: Promoting open and transparent government-industry collaborations
Enabling the all-important government-industry collaborations needed to create the frameworks that make it possible to build truly open, innovative and future-proofed national ID systems, OSIA is transforming how governments leverage ID to deliver real-world impacts for their citizens and national economies.

OSIA: An Overview
To solve the interoperability challenges within the identity sector, the OSIA initiative is focused on a clearly defined scope of work:
1. Build a common understanding of the functional scope for identity systems building blocks
OSIA’s first step has been to formalize the definitions, scope, and main functionalities of each building block within the identity management system.
2. Create a set of standardized interfaces and data dictionary
For this core piece of work, OSIA is focused on developing the set of interfaces and standardized data dictionary needed to connect the multiple identity system components and ensure seamless interactions via pre-defined services.
It is then down to each government to define and implement the interaction processes between individual components (which in turn determines which interfaces are associated with each component), according to local laws and regulations.
OSIA: Interfaces to date
OSIA Benefits
Initiating a pragmatic approach that assures interoperability and harmonization across the extended ID ecosystem, OSIA delivers benefits for a multitude of stakeholders.
Unleashing market innovation
By delivering interoperability among vendor solutions, thanks to the development of open standard interfaces, OSIA both establishes the conditions that support an equal marketplace and makes it possible for the wider identity community to collaborate in new ways.
- Create a marketplace where all vendors can compete equally
OSIA operates at the interface layer and does not define – or therefore favor - any technology at the component layer (which is typically where the differentiation among vendors takes place). Equal competition among vendors is therefore assured.
- Support the emergence of new local market models featuring local suppliers and SMEs
Like the Open Banking revolution, OSIA exposes high performing standardized interfaces that will enable new use cases and market offers – from the simple to the complex.
- Ensure product(s) compatibility after Mergers & Acquisitions
Market consolidation can often lead to major products being put into maintenance – leaving governments with little choice but to replace these. Now, thanks to OSIA’s open standards, whatever the status of a product, it will continue to be interoperable with new offers.
Address integrator/ vendor lock-in
Injecting new levels of flexibility and openness, OSIA enables governments to leverage industry expertise and exert full control over their sovereign identity systems. So they can pursue their national development agendas - without any fear of integrator/ vendor lock-in.
With OSIA, governments are no longer forced to implement a wall-to-wall solution from a single vendor and will not encounter compatibility difficulties when evolving their existing legacy solutions.
In other words, OSIA gives governments the freedom to:
- Implement multi-vendor programs by mixing selected components from different suppliers.
-
Extend legacy solutions or replace legacy component(s) with a new component(s) from a different supplier(s).
Enabling identity as a service
Providing a universal framework that makes it possible for governments to initiate digital ID and services for all, OSIA empowers governments to build the foundations for a smarter citizen ID future. Whether that is unleashing new inclusive eGovernment solutions that give citizens ease of access to public services. Or enabling trusted digital ID schemes that extend the use of citizen ID into other online areas - such as banking and payments.
- Drive digital ID market growth
OSIA facilitates the link between sovereign identity management solutions and digital identity solutions, like mobile ID, by standardizing the ad hoc interfaces that decouple providers of the ID management solution and the digital ID solution.
- Reduce fraud within siloed databases/multiple ID systems
OSIA enables the secure and controlled flow of data and services, like ID deduplication and authentication, across multiple foundational and functional registries – even where these registries are run by separate ministries and government agencies. Armed with these capabilities, governments are able to reduce public sector payroll fraud, reduce leakage in public benefits and social protection disbursements, reduce fraud associated with tax filing and ensure the integrity of the electoral process by reducing voter fraud.
OSIA and digital ID
Identity verification and document authentication
ID Usage consists of a set of services implemented on top of identity systems to favour third parties consumption of identity data. The services can be classified in three sets. The first, the Relaying Party (RP) API is provided within the OSIA framework, with the second and third – Digital Credential Management and Federation Services – delivered within an extended framework of ISO and Open ID Connect standards.
OSIA Relying Party API: submitting citizen ID attributes for validation
The purpose of the OSIA Relying Party (RP) API is to extend the use of government-issued identity to registered third party services. The individual will submit their ID attributes to the relying party in order to enroll for, or access, a particular service. The relying party will leverage the RP API to access the identity management system and verify the individual’s identity. In this way, external relying parties can quickly and easily verify individuals based on their government issued ID attributes.
- Example use case application: telco enrolment
The RP API enables a telco operator to check an individual’s identity when applying for a service contract. The telco relies on the government to confirm that the attributes submitted by the individual match against the data held in the database therefore being able to confidently identify the new subscriber. This scenario can be replicated across multiple sectors including banking and finance, airlines, hospitality, aid agencies and many more.
ISO Digital Credential Management: delegating digital issuance to third parties
The purpose of the Digital Credential Management is to enable external wallet providers to manage government issued digital credentials distribution, storage and usage. The OSIA specification points to the ISO ISO22230 standard.
- Example use case application: digital driver license
The DCM enables individuals to request a digital driver license as a digital credential in their selected wallet to use for online and offline identification.
Open ID Connect Federation: user-initiated attributes sharing
The purpose of federation is to enable the user to share their attributes with a chosen relying party using well-known internet protocol: OpenID Connect. The relying party benefits from the government’s verified attributes.
- Example use case application: on-line registration to gambling website
Here, the Federation service enables individuals to log-in with their government credential (log-in/password) and share verified attributes ex. age (above 18) with the relying part.
OSIA is not a new concept
Watch webinar on Open APIs as a Pathway to Identity and Sectorial System Development
Harnessing open APIs to unlock value, fast track transformation, increase the agility of service development, and build deep and integrated identity systems isn’t a new notion.
Other industries have already seized on the transformational power of APIs to:
- easily share information across applications, services and systems – even legacy systems
- rapidly scale and evolve their systems and services to meet new requirements
- bring new products and services to market
Let’s take a look at just two sectors that are using APIs to unlock new value, and to build and connect modern applications to one another – and to the data and services that power them.
Telecom
The telecommunications sector is deploying open APIs to enable rapid, repeatable, and flexible integration among operations and management systems that make it easier to create, build and operate complex innovative services.
Collaboratively developed by stakeholders from across the industry, the TM Forum’s Open API suite of 50+ APIs are propelling innovative new digital services in a number of key areas – including IoT applications, smart cities, mobile banking and more.
Open Banking
Powered by APIs that facilitate the flow of data and make it possible for banks to securely share customer information with verified third-party service providers, the Open Banking revolution is enabling banks to build new digital ecosystems and adapt fast to business and consumer demands for innovative services that save them time and money.
Whether that’s seeing all of their accounts, savings and credit cards in one place – regardless of who they bank with. Or tracking their payments to gain insights on spending patterns. Or determining their creditworthiness and demonstrating their eligibility for a range of financial services.
The evolution of the Open API Economy
Open APIs are now major enablers of full scale digital transformation across both public and private sectors. Beginning in the early 2000s as internal initiatives within technology companies, Open APIs evolved rapidly as online eCommerce giants like Amazon recognized the opportunities of levering this approach to open up systems and data to their merchant base. Today, we see a wealth of exciting new initiatives – not least open banking – being driven by a ever-evolving Open API ecosystems. Now, as adoption of OSIA grows across the world, we are witnessing the rapid growth of an Open API ecosystem coaleccing around Identity Management – and though this, the ability to create truly inclusive and more efficient public services.

The use of false identities is a problem that goes far beyond the area of border control. Though fraudulent identification documents are commonly associated with issues like immigration, they can also be used to aid serious organised crime, terrorism, fraud, and a range of other threats. As a result, accurate verification of identity documents is now a major concern in additional contexts including areas such as financial services and digital retail.
'Authentication: Are You Who You Claim to Be?'is a new guide from the SIA that addresses the challenge of identity authentication. Discussing the inherent difficulty in validating someone’s identity, as well as some of the solutions that are currently available, the report also provides detailed use cases and recommendations for anyone who may be looking to improve their understanding of this critical practice.
“It is very useful and highly informative report providing answers to questions concerning the Optical Machine Authentication (OMA) and in turn highlighting its increasing role in document authentication. The report will help practitioners expand their understanding of benefits and challenges linked to the increased use of optical authentication technologies.”
Malik Alibegovic, INTERPOL CCSD
In this blog, we provide a summarised view of some of the key themes covered in the guide.

Facial Recognition (FR) has evolved considerably in recent years and has many important potential benefits such as ease and security of use, privacy protection, and the detection and deterrence of crime. However, it can also be used excessively and intrusively and needs to be used appropriately, in circumstances that are justified and in accordance with good privacy laws and principles.
The SIA believes that recent moves to ban facial recognition technologies in a number of US states are premature. Similarly, in the EU, recent proposals regarding the development and use of artificial intelligence (AI) systems classify those intended to be used for remote biometric identification as ‘high risk’. If adopted, these systems would require a stringent ex-ante conformance assessment.
Pressing the pause button without a reasoned debate on privacy and civil rights, or on the potential IP and sovereignty issues of greater regulation, represents a potentially backward step for public safety that also limits the abilities of companies to transact securely with consumers in the digital world. See our blog on artificial intelligence here.
Facial recognition technologies have proved invaluable during the COVID-19 pandemic, making it possible for citizens to enrol remotely for services and verify their identity.
The SIA believes it is up to the authorities to play their role as regulators and to define the limits and conditions of use of facial recognition technologies, working with the industry to put in place governance frameworks that address the concerns of all stakeholders.

As governments and NGOs look to health certificates as a response to the challenge of safely reopening borders and reinstating freedom of movement for citizens, there is now a very real urgency in consolidating approaches, agreeing standards and achieving interoperability. Failure to do so will reduce international acceptance and threaten to derail these important initiatives. Here, we take a look at the key issues.
Health certificates schemes promise to streamline how people demonstrate they are unlikely to either catch or spread a particular disease, or diseases. While not a new concept, the COVID-19 pandemic has brought discussions of wider adoption and standardized adoption into sharp refrain.
In today’s context, these schemes use physical and/or digital certificates to make it easier for airlines, airports, border control agencies and others to verify whether a certificate holder has been vaccinated against COVID-19, has tested negative for the virus, or has recovered from it.
The increasingly widespread introduction of these certificates has allowed governments to lift a number of pandemic-related restrictions – from cross-border travel to attending large public gatherings such as sporting events.

On April 21, 2021, the European Commission proposed new rules and actions on the development and use of artificial intelligence (AI) systems with the stated objective to “turn Europe into the global hub for trustworthy artificial intelligence”.
Following a risk-based approach, the proposals will ban those AI systems considered a clear threat to the safety, livelihoods and rights of people. Others will be rated on a risk scale from high to minimal. In particular, all remote biometric identification systems are considered high risk and subject to strict requirements.
Secure Identity Alliance (SIA), whose members are European and global leaders in this fast-emerging space, are supportive of the principles to ensure excellence and trust in AI systems, and believe a fit-for-purpose framework has the potential to become an adopted standard around the world – as has been the case with the General Data Protection Regulation.
However, SIA believes that the rules governing the development and provision of AI systems should be proportionate.
As the proposals stand today, there is a concern that some rules threaten to stifle innovation and therefore undermine the stated goals of the Commission and the position of Europe as a leader in this critical field of technology.

The National Agency for Economic and Social Inclusion in Guinea (ANIES) will leverage the OSIA open standards approach to create a fully interoperable identity system.

President of the Federal Republic of Nigeria Muhammadu Buhari is showing the NIMC (National Identity Management Commission) NIN (National Identity Number) slip – that can be verified against the central national ID database leveraging OSIA interface

By Joachim Caillosse, Chair of the Secure Document Working Group of the Secure Identity Alliance
An in-depth new guide to help tackle passport booklet fraud
Document fraud is a serious crime, one that has implications that stretch from personal identity theft all the way through to national security. Moreover, document fraud often serves as the foundation upon which other threats are built – human trafficking, drug smuggling, and terrorism amongst them.
Passport fraud is a key part of this landscape, and a growing problem. While Covid-19’s debilitating affect on international travel has helped to slow the rise of passport fraud over the past 12 months, the longer-term picture tells a different story altogether Some 100m travel documents were reported lost or stolen in 20201 and according to Frontex Risk Analysis, passports represented 47% of the fraudulent documents detected at European Union external borders in 2019, leading some commentators to decry a growing passport fraud “epidemic2”.
Ever keen to raise awareness of identity-related threats and provide guidance on the latest defences and countermeasures, the Secure Identity Alliance (SIA) has this week launched its “Passport Fraud Trends and Ways to Combat Them” report – a comprehensive overview of the current travel document security landscape.

By Michael Brandau, Chair of the Secure Identity Alliance's Border Working Group.
With technology, Covid-19, and a number of other factors driving major change at the border, the Secure Identity Alliance has updated Strong Identity Strong Borders, a guide designed to help anyone who wants to understand the subject more, but who is not an expert.
Strong Identity, Strong Borders introduces the key concepts and explores the evolution of border control, and how those responsible for safeguarding their territory can embrace new approaches around identity in order to create secure, seamless, and streamlined passenger experiences.
Today the refreshed Principles on Identification for Sustainable development were published. Secure Identity Alliance is proud to have once again been asked to contribute to this important body of work to ensure that these updated Principles reflect today’s changing world and its own vision of supporting the provision of legal, trusted identity for all.
Five years ago the Secure Identity Alliance, along with other organisations committed to the development of ID systems that are inclusive, trusted, and accountable and supported the development of a set of shared ‘Principles for Good Identification’.

by Kristel Teyras, Chair of the Digital ID Working Group of the Secure Identity Alliance
With governments poised to accelerate national digital ID programs, the SIA commissioned a study to uncover lessons learned from innovative, real-life digital ID deployments around the world.
Providing unprecedented ‘on the ground’ insights and perspectives, the study produced in partnership with onepoint gives a unique voice to stakeholders from 25 innovative sovereign digital ID schemes. Their shared learnings highlight the guiding principles and good practices that are critical for driving usage, adoption, and success – regardless of the digital ID model adopted.