Understanding Public Key Infrastructure (PKI) in Passport Management
Secure ePassport chips result in trust and efficiency
What is ‘PKI’? An introduction
This article can be downloaded default HERE(2.26 MB)
Trust in passports is essential. PKI technology gives strong evidence that information on a secure passport chip can be trusted. This helps authorities issue more secure passports, increase security and throughput at the border, increase automation and catch identity cheats. It can help airports, airlines and commercial parties to check documents and carry out KYC (Know Your Citizen or Know Your Customer). Genuine passengers are more able to demonstrate their true identity quickly. Conversely, identity cheats stand more chance of being discovered.
Threats of passport fraud are real! A genuine document can be lost, stolen or borrowed and used by someone who is not the holder (an imposter or lookalike). A criminal might try to change the photograph or other data about the holder, to turn a passport into his own travel document (a forgery). A false passport might be manufactured (a counterfeit). Someone may make a false application to obtain a passport (a Falsely Obtained Genuine (FOG)). Or someone may steal blank passports which have not yet been personalised (had the holder’s details applied).
Great care is taken to defend passports from such attacks. This includes strong security on the manufacture, storage and delivery of documents; rigorous testing of new passport applications; and advanced security features in passports so that false documents are difficult to produce or use. See Passport Fraud Trends and Ways to Combat Them (Secure Identity Alliance (SIA), 2021); and ICAO 9303 Part 2: Specifications for the Security of the Design, Manufacture and Issuance of MRTDs (see references).
Secure chips improve security and convenience
Many passports and ID cards contain a chip, holding key data about the document and the holder, including the holder’s facial photograph. All of this data is protected by the issuer who includes a cryptographic digital signature on the chip. This signature, when verified, shows that data on the chip comes from the right source and has not been changed. Only the issuer can produce this signature, but everyone who needs to can verify that the signature and the data match. If so, it can be trusted; if not, it can’t. The complete picture is called a Public Key Infrastructure (PKI).
Here is a simplified, high-level description of how this works:
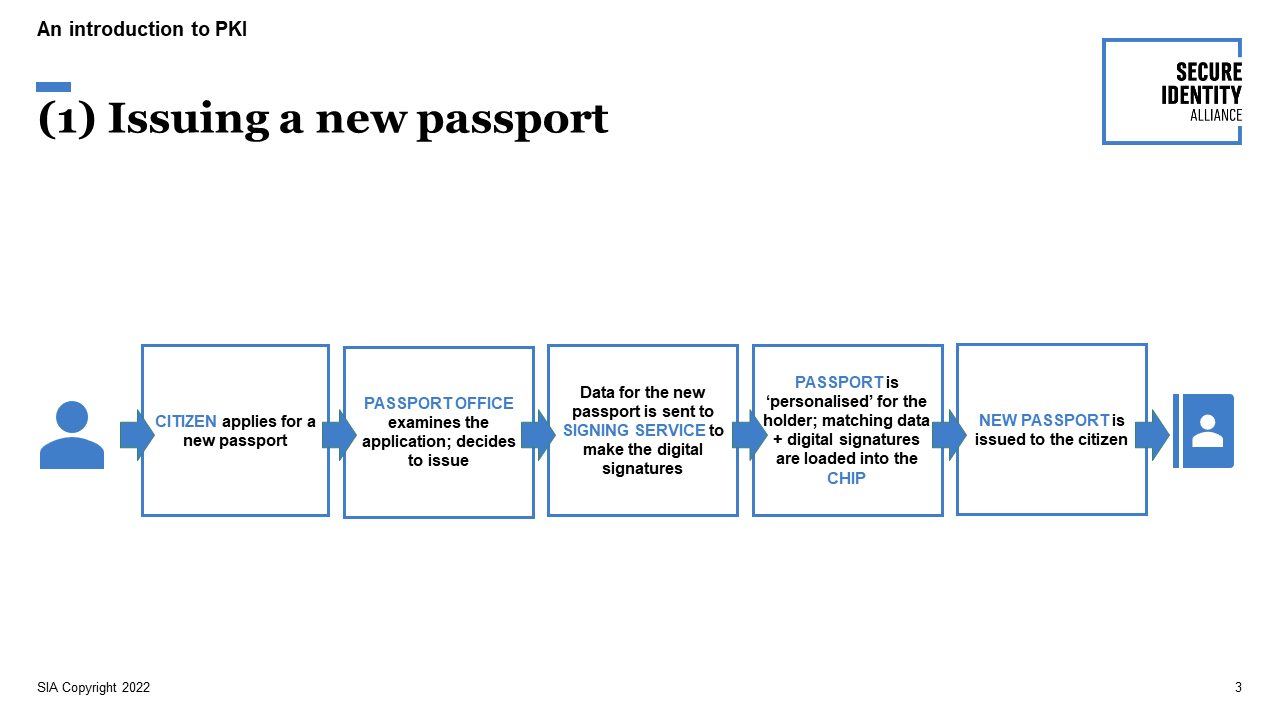
(1) Issuing a new passport—signing data and loading it into the secure chip
When someone applies for a passport and the application is accepted, information is prepared to appear in the physical document. A copy of the same data is made to go on the chip. A signing service then uses cryptography to generate digital signatures relating to the data. During personalisation, the information is written onto the blank passport, and the data including digital signatures are loaded securely onto the chip.
(2) Enabling authentication around the world—publication via the ICAO PKD
The passport issuer publishes a CSCA Country Signing Certificate, containing a public encryption key which validates signatures against the data they protect. However, that key does not let anyone generate a valid signature if data on the chip were changed—only the issuer can generate valid signatures, using the corresponding private key. Certificates, with their public keys, can be shared via the ICAO Public Key Directory (PKD).
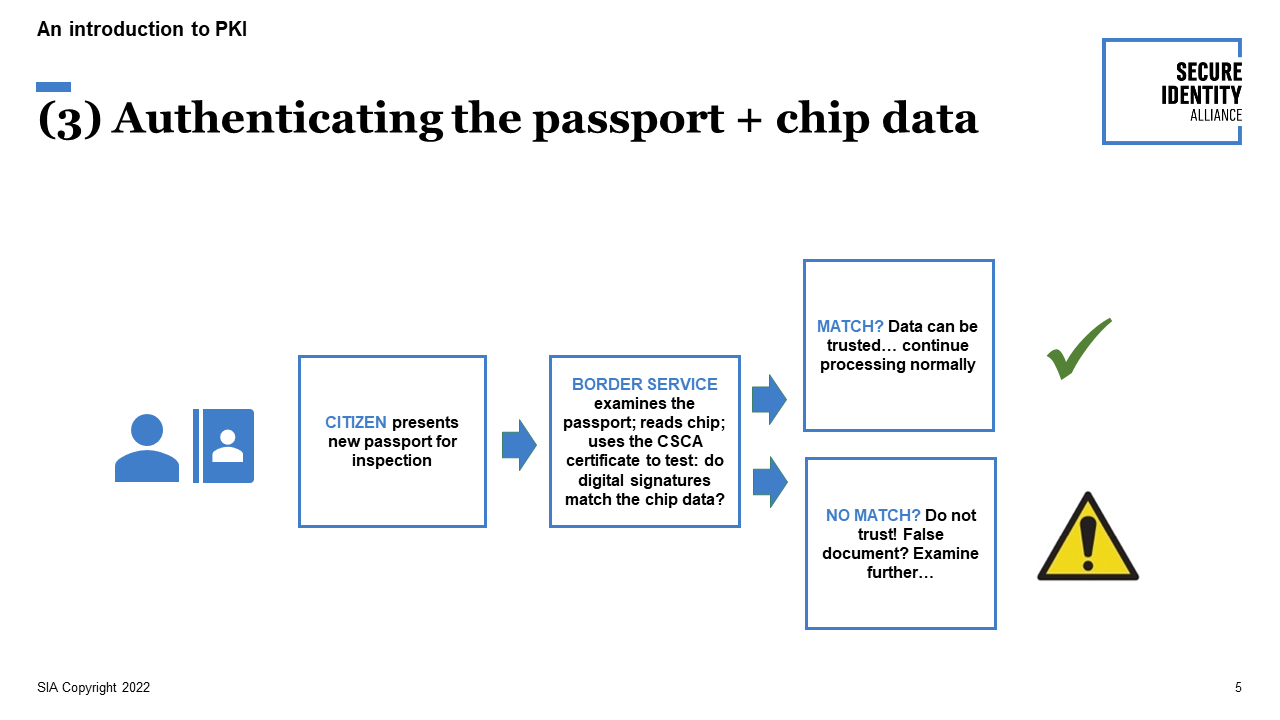
(3) Authenticating the passport + chip data—testing a passport at the border
When the passport is presented at a border the passport is inspected. Data on the chip is read and validated against the digital signatures. If the signatures do not match the data, this alerts the border service that the passport may be false and should not be trusted.
What is in a digital signature?
A digital signature is an encrypted representation of some data that it protects. All of the data is processed to produce the signature. Provided security is maintained, only the genuine issuer can produce a genuine digital signature. If any of the data is changed after it is issued (example: substituting a different name or facial photo), when the signature is compared against the data it will not match, revealing that it cannot be trusted.
This is achieved by using the special form of encryption described after.
Cryptography is the key
For PKI, a smart form of encryption is used which uses a pair of encryption keys, one named “public” and one named “private”
- The issuer holds a secret private key, which is used to make the digital signatures for the chip—an operation called ‘signing’ the data.
- The corresponding public key within a certificate allows anyone to verify that the digital signatures correctly match the data on the chip and comes from the authentic source, but does not allow anyone to create genuine signatures, for example for false data.
- Two-key encryption like this is called public key encryption, and the complete end-to-end infrastructure is known as a public key infrastructure (PKI).
- The ICAO Public Key Directory (PKD) is a convenient and secure means of publishing all necessary public keys within their certificates. This is an efficient one-stop shop for passports issuers and border services to exchange the data they need to share, though not all certificates are distributed this way.
- Each issuer operates a highly secure Country Signing Certificate Authority (CSCA) which holds the ‘master’ signing key for the country to validate up to 5 years of document signing. The CSCA is the root of trust in the system and issues signed public key certificates (containing the public key) to the ICAO PKD or others.
Specifications
ICAO 9303—global specification for passports including secure chips, by ICAO. See References.
Technical Guidelines on inspection, from ICAO and the German Federal IT Security Agency (BSI).
Protection Profile—required security features to protect secure chips in passports / eMRTDs.
Extended Access Control (EAC)—extends ICAO 9303 to protect access when other biometrics of the holder are included on the chip. An EU version is mandated for EU passports, containing two fingerprint images of the holder.
Algorithms for public key encryption—the first commercial public key algorithm was RSA (Rivest, Shamir and Adleman); more recently, Elliptic Curve algorithms.

Making PKI effective
Passport PKI works well if it is correctly and securely implemented. This includes:
- Good understanding of the complex technology and communications infrastructure for PKI, end-to-end, in the design and operation of the system, complying with ICAO 9303 and other relevant standards and good practice.
- Strong IT security, including protecting against unauthorised access and cyberattacks, protecting private keys and critical functionality in Hardware Security Modules (HSMs).
- Joined-up working between stakeholders including management and technical; and issuance and authentication. Non-expert stakeholders need the opportunity to understand key aspects of PKI in accessible terms so they can make informed decisions—bridging the gap between specialists and non-specialists.
- Membership of ICAO PKD and ensuring that new public keys are uploaded and shared in time to reach border services before they are used to sign new passports.
- Active management to acquire all public key certificates possible (see note, below).
Some recent updates
The ICAO PKD enables participating states (82 in February 2022) to share their respective public keys to enable easier controls around the world.
A recent initiative of the ICAO is to make the public keys available to the Private Sector - commercial entities like banks, insurance, travel companies… so more actors can verify data contained in the chips of ePassports. This generates facilitation and trust. See: Pilot project - Authorizing use of data from the ICAO PKD by the Private Sector.
The future?
ICAO are co-ordinating efforts to introduce a future form of the passport which will include a virtual component: the Digital Travel Credential (DTC). It could be possible for travellers to send the contents of their DTC electronically to the border services at their destination in advance; and it may be possible for a mobile phone to become an accepted form of passport in the future. The data structure of a DTC is similar to a standard ePassport, so it can also be verified using the PKD. See SIA Blog on DTC here.
Computer power increases substantially over time (known as Moore’s Law), so what is considered ‘beyond computation feasibility’ to break today may become unsafe in the future, requiring key lengths to be increased. Quantum computing may radically increase computer power beyond the existing trend. New forms of encryption are being standardised to safeguard trust in the era of quantum computing.
Conclusion
The PKI model described in this paper gives assurance that data stored in the document chip are genuine. The key issue is trust. Implemented well, PKI can strengthen confidence in an identity presented at a border and in many other use cases.
Further reading is given in the References, below.
Talking to the chip
Communicating with the secure chip in an e-passport uses Near-Field Communication (NFC) - low-powered radio signal used when a payment machine talks to a contactless card.
Several steps should be followed to read and authenticate an e-passport securely.
(1) Establish contact with the chip
A reader can use two mechanisms to access the chip: the original, Basic Access Control (BAC) is being replaced over time by Password Authenticated Connection Establishment (PACE). PACE-only documents have been allowed since 2018 so readers already need to be able to read both. The term Supplemental Access Control (SAC) refers to using PACE when both parties can do so, or BAC if not.
These steps read the data on the chip, but they do not check whether the data and chip are genuine: whether the e-passport can be trusted. Experts agree with ICAO recommendations that further steps (2) and (3) to authenticate the document are essential.
(2) Authenticate the data on the chip
After connecting to the chip, the reader verifies that the digital signatures correctly match the data on the chip. A correct match is essential as it proves that the data has come from the right originator and has not been amended, so can be trusted. This step is called Passive Authentication (PA).
PA involves two levels of signing and authentication. Document signing keys are used to sign individual passports but are typically used only for a limited number of times before being retired. The document signing certificate stating the public key for a passport is included in the chip, and this certificate is signed by the country signing key which is used to sign document signing certificates, for a maximum of 5 years.
Certificate Revocation Certificates (CRLs) and Deviation Lists are used by an issuer used to notify all countries of technical errors or certificates that should not be relied on (for example because security has been compromised). These are notified to ICAO for inclusion in the PKD, so that Passive Authentication can ensure it does not place trust in invalid data.
Master Lists can be included in the PKD which declare which public keys that country considers valid—this is useful as a consistency check but is one country’s view rather than ICAO’s.
(3) Authenticate the chip
Another test is carried out to check that the good data has not been copied (cloned) onto a false chip. This test is called Chip Authentication (CA), or an earlier version, Active Authentication (AA).
After (2) and (3) have been successfully completed, the reader now has evidence that the chip and its data can all be trusted.
(4) EU fingerprints access
EU passports contain two fingerprint images of the document holder, to enable a simple and effective check on identity if necessary. This is subject to rigorous privacy control called Extended Access Control (EAC). The process to verify this permission and unlock access to the fingerprints is Terminal Authentication (TA). EAC requires the reading country to have authority from the country issuing the document: permission is exchanged via a Single Point Of Contact (SPOC) in each country.
Some further notes and examples
The basis for ePassport PKI and the use of public key encryption is a strong basis for security and can be used in a number of other forms.
Visible Digital Seal (VDS)
This security solution uses PKI to sign and authenticate data on printed or visually represented documents such as a visa. VDS uses a QR 2D barcode. The barcode, when used to encode visa information, contains data such as the visa number, date of issue and the holder’s name and passport number; plus a digital signature. A barcode like this cannot hold as much data as a passport chip. The barcode is read optically by the reader device, and then the signature is verified as for a passport chip. The relevant public key(s) are needed to verify a VDS, either from the ICAO PKD, or an alternative secure source. See references. New EU visas will include a VDS.
Two VDS standards have been defined: (1) the original version, in ICAO standard 9303 Part 13, used for visas and emergency travel documents; and (2) VDS-NC V1.3, used for vaccination / health certificates and for Digital Travel Authorisations (DTAs). These two are similar, but with some technical differences and additions. (NC stands for Non-Constrained.)
EU COVID Certificates (EUCC)
The PKI model used for these certificates has been successfully used at European level as part of the definition of QR Codes used to confirm vaccination, test results and recovery from COVID.
ICAO PKD can include certificates that can support verification of EUCC, VDS, VDS-NC and other health proof formats, as for ePassports and other ICAO-complaint electronic travel documents.
Full coverage?
Not everyone issuing documents submits their public key certificates to ICAO for publication on the PKD. Active management is therefore needed to check for omissions, followed-up via other collections, analysis of Master Lists (ML) and/or bilaterally to acquire the full range of certificates possible, so that the maximum number of passports and other documents can be securely authenticated at your country’s border.
EU identity and travel documents
The EU has strengthened European ID Cards and certain Residence Documents, bringing these into line with European Passports and Residence Permits which implement ICAO 9303 plus the EU requirements for fingerprint images (EAC, above). This is contained in EU Regulation 2019/1157, in force from 2 August 2021.
Logical Data Structure (LDS)
This specifies how data is stored on a secure passport chip (an eMRTD), as defined in ICAO 9303. Data Groups in the LDS hold data about the document, e.g.:
DG1 holds a copy of the Machine Readable Zone (MRZ); DG2 the facial image of the holder; DG3 fingerprints; DG4 eyes / iris; and the Security Data (SOD) holds the digital signatures.
PKI, in general
The core method used in PKI is also used to authenticate electronic messages and online transactions, and to create electronic digital signatures for example to secure a document in its original form or to confirm someone’s agreement to a contract.
A Last Word
We hope this short note gives some helpful insight to the technical complexity of PKI. However, the advice remains that implementing PKI must be done securely: this is complex and must be done with full engagement of experts.
Glossary
BAC Basic Access Control (to communicate with the chip)
CA Chip Authentication (checks that a chip is genuine, not a clone)
CSCA Country Signing Certificate Authority, the root of trust in a country’s PKI
DG Data Group within the LDS, e.g DG-1 (MRZ), DG-2 (face image), DG-3 (fingerprints)
DTA Digital Travel Authorisation
DTC Digital Travel Credential
EAC Extended Access Control (uses TA)
EUCC EU COVID Certificates
eMRTD electronic Machine Readable Travel Document: ICAO 9303 passport, ID card
ePassport Equivalent to eMRTD, in the case of a passport
ICAO International Civil Aviation Organisation
KYC Know Your Citizen, or Know Your Customer
LDS Logical Data Structure—how data is structured within the chip
ML Master List—public keys etc. of other countries used by an issuing country
MRZ Machine Readable Zone—2 or 3 lines of data on the title page of an eMRTD
NFC Near-Field Communication (low-powered communication from the reader to chip)
PACE Password Authenticated Connection Establishment (more secure form of BAC)
PA Passive Authentication (tests that data on the chip matches the digital signatures)
PKD Public Key Directory
PKI Public Key Infrastructure
PP Protection Profile—security specification for an eMRTD chip
QR A format of 2-D barcode (QR = Quick Response). See VDS.
SAC Supplemental Access Control: uses PACE; or if not possible, BAC
SOD Security Object—digital signatures held in the LDS on a chip
TA Terminal Authentication (used in EAC to unlock access to fingerprints)
VDS Visible Digital Seal: uses a QR barcode with a digital signature for authentication
References
ICAO: Basic Concepts of MRTD and EMRTD—Two page factsheet
https://www.icao.int/meetings/tag-mrtd/tagmrtd22/tag-mrtd-22_wp24.pdf
ICAO Doc 9303, Machine Readable Travel Documents, 8th edition 2021, contents page…
https://www.icao.int/publications/pages/publication.aspx?docnum=9303
… Doc 9303, Part 2, Part 2: Specifications for the Security of the Design, Manufacture and Issuance of MRTDs
https://www.icao.int/publications/Documents/9303_p2_cons_en.pdf
… Doc 9303, Part 11: Security Mechanisms for MRTDs
https://www.icao.int/publications/documents/9303_p11_cons_en.pdf
… Doc 9303, Part 12: Public Key Infrastructure for eMRTDs
https://www.icao.int/publications/Documents/9303_p12_cons_en.pdf
… Doc 9303, Part 13: Visible Digital Seals
https://www.icao.int/publications/Documents/9303_p13_cons_en.pdf
ICAO Master Lists, ePassport and Health
https://www.icao.int/Security/FAL/PKD/Pages/icao-master-list.aspx
German Federal Office for IT Security (BSI):
BSI TR-03135 Machine Authentication of MRTDs for Public Sector Applications
https://www.bsi.bund.de/EN/Service-Navi/Publications/TechnicalGuidelines/TR03135/TechnicalGuidelines_03135_node.html
EU Digital COVID Certificate
EU Digital COVID Certificate | European Commission (europa.eu)
Secure Identity Alliance, Passport Fraud Trends and Ways to Combat Them
https://secureidentityalliance.org/utilities/news-en/entry/passport
Secure Identity Alliance, Strong Identity, Strong Borders
https://secureidentityalliance.org/utilities/news-en/entry/strong-identity-strong-borders-sia-report
Secure Identity Alliance, Authentication: Are You Who You Claim to be?
Secure Identity Alliance, Giving Voice to Digital Identities Worldwide
Secure Identity Alliance, Biometrics in identity: Building inclusive futures and protecting civil liberties
This paper was produced by the Document Security Working Group of the SIA, Chair: Joachim Caillosse; Lead Author: Frank Smith, SIA Advisory Observer. Thanks for all comments and contributions for the paper including those from colleagues outside the SIA.
It was initially published on Keesing Platform in two parts: Part 1 and Part 2
May 2022